120 million of spam messages pointing to 15 domains
In our dataset, we’ve collected more than 120 million email messages delivered by the botnets with malicious links of any kind.

February 24, 2020
At Virusfree.cz we’re constantly trying to understand current threats and improve our detection. To do so, we operate several services our clients most likely never knew they exist. Recently we have analyzed the URL links in the messages the botnets are trying to deliver for the last month.
 |
In our dataset, we’ve collected more than 120 million email messages delivered by the botnets with malicious links of any kind. The sampling interval was between January 19th, 2020 and February 17th, 2020. |
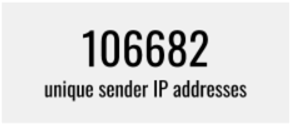 |
We have identified the sending IP addresses. There are hundreds of IP addresses that attempted to send just one message and 7 IP addresses that sent more than 100000 messages. |
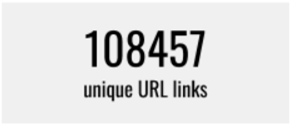 |
While analyzing the URL payloads we have understood that from all the more than 120 million messages we see about 108 thousand unique URL links in the messages. |
Let’s break this all down. URLs in the dataset can be clustered by the similarities and just by plain look at the URL structure we’ve found a large group of URL entries that attracted our attention. This type of structure had a majority in the dataset, more than 94 million entries, almost 79%, but only 10032 unique URL links, which is below 10% of the whole volume.
By crawling these links of which about 30% were already inactive (the website operator deleted the files) we found out that the file size barely exceeds 200 bytes. The content of the files keeps the same structure.
The URL parameter value in the file is variable, the pointing URL can also contain parameters, subdomains, etc. The final list of target domains contains only 15 entries (the first column represents the number of occurrences):
| 4614 | t500track3[..]com |
| 626 | your-prizes-here[..]com |
| 424 | yummyplaymatesfinder[..]com |
| 367 | royalmagicvip[..]com |
| 293 | royalboomcas[..]com |
| 176 | newmedsdeal[..]eu |
| 137 | helper-cbd[..]world |
| 136 | yourdatingstores1[..]com |
| 109 | win-big-bonus12[..]com |
| 81 | gambling[..]pro |
| 67 | curingcaretrade[..]eu |
| 57 | prize-outlet4[..]life |
| 3 | fokefoto[..]vip |
| 1 | hookupdate365[..]com |
| 1 | datinglocator24[..]com |
As you can see, the initial more than 94 million entries related to a single URL structure are shrinked to only 15 real domains the attacker uses.
PS: From the remaining 25 million entries, at least 13 million points (by various means, hidden in URL shorteners, redirects or directly ) to some of the above-listed domains.